In today’s data world, data breaches are commonplace. Not a day goes by without a headline about a massive data breach. Just to put this into perspective, there have been more than 14 billion records lost since 2013. The leaks come from both insiders and outsiders - whether they are accidental leaks or malicious activities like phishing and malware.
All enterprises are in the cloud and so is their sensitive data. According to a recent McAfee survey - 97% of organizations use cloud services (public, private or hybrid) and 83% store sensitive data in the cloud. For enterprises where “data is the new oil”, data leaks can be devastating, costly and a nightmare to your reputation. IT leaders are increasing budget (Increase to 37%) and slowing the adoption to the cloud (40% of the IT leaders in the same survey) to mitigate the risks. Even with these mitigations, 1 in 4 enterprises has experienced data theft from their cloud.
So how does Gamma solve this problem?
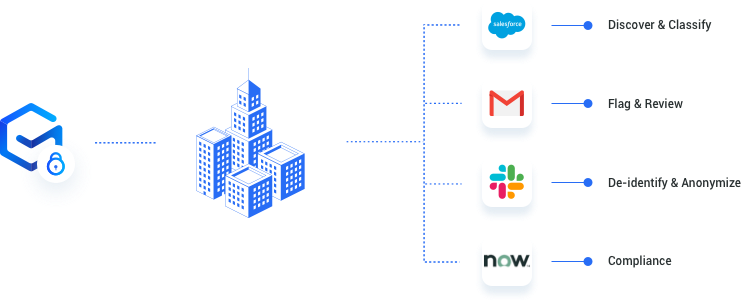
Gamma uses the following four-step process to protect your data.
- Discover & Classify: Understanding and knowing your data is the foundation for data security. Gamma connects to your SaaS applications (Gmail, Slack, Salesforce or others) and automatically discovers the data. Using machine learning and AI, Gamma classifies and/or flags sensitive data.
- Flag & Review: Gamma provides a simple and easy-to-use dashboard to monitor sensitive data, its location, and users. The dashboard also allows you to easily flag and/or define the rules for the sensitive data.
- De-Identify & Anonymize: Once sensitive data has been identified, Gamma helps defend this data. Gamma lets you - de-identify, anonymize, pseudo anonymize or simply block the sensitive data.
- Comply: The data, users and corresponding actions are all logged. Gamma provides a continuous monitoring dashboard and audit reports to ensure compliance with various regulations like PCI, GDPR, and CCPA among others.















